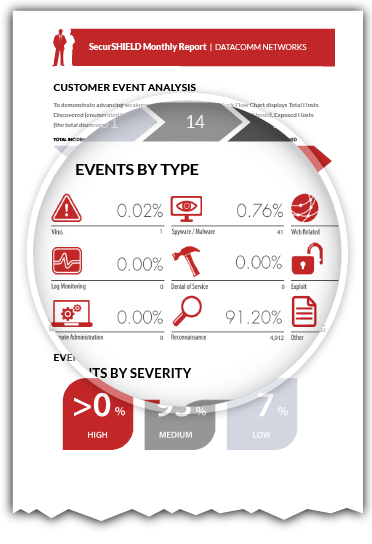
Intrusion Prevention: Monitoring network activity 24x7x365
It is quite common for businesses to put locks on their doors and windows, subscribe to a security service and even install cameras that record all traffic entering and exiting the building. Unfortunately this same attention is not given to most computer networks. Usually a firewall is present on the perimeter – sometimes an intrusion detection sensor is installed. Many times, however, these measures are neglected after initial installation, leaving the company vulnerable, but unaware, until an attack takes place.
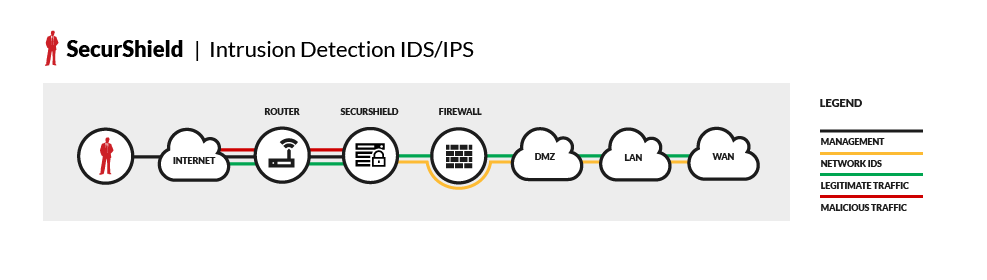
DataComm’s Intrusion Detection and Intrusion Prevention Services, SecurShield, pairs a best-of-breed device with best-in-class service. Our proprietary device has the ability to monitor activity on multiple network segments with real-time intelligent blocking of suspicious activity. DataComm’s Secure Network Operations Center is staffed 24x7x365 with certified security technicians that interpret the suspicious activity and respond to threats in a customer-specified manner.
Service Features
- Comprehensive Monthly Logs
- Updates (Software, Signature and Rules)
- E-Mail Summary Reporting
- Real-Time Reporting and Management
- Around the Clock Protection
- DataComm’s SecurSensor is the best network security device on the market – a proactive inline intelligent IDPS (Intrusion Detection/Prevention Sensor) that uses a powerful combination of signature, protocol and anomaly-based inspection methods to achieve the maximum attack detection and prevention capability.
SecurSensor Features
- Real-time Intrusion Detection, Prevention and Response
- Resistance to Evasion Techniques
- Secure Website Monitoring
- Signature and Anomaly Sensing
- Integrated IP Address Lockout
- Scalable Internal Sensing Presence
Firewall Management: Place your network in the hands of certified professionals
Firewalls have been the cornerstone of network security for over 20 years and will continue to play a vital role in protecting your network infrastructure from external threats in the future. As firewalls continue to evolve, their feature do as well – ever increasing the complexity of firewall management.
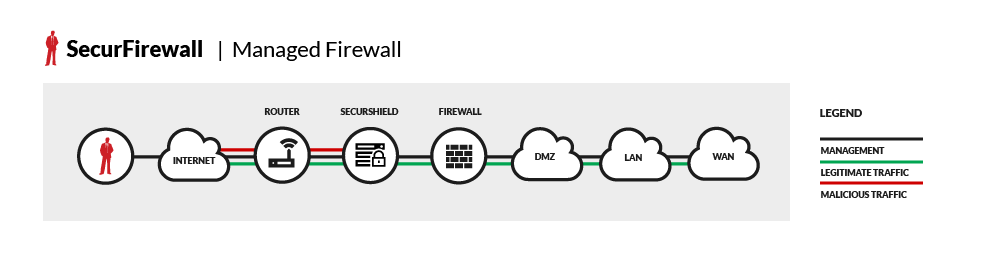
DataComm’s Firewall Management Solution was designed to reduce the complexity of monitoring, maintaining and utilizing the built-in feature sets by providing:
- Rules/Policy Changes
- Patch Management
- Performance Monitoring
- Availability Monitoring
- Fault Notification
- Network Troubleshooting
- Advanced Reporting
DataComm will remotely monitor your firewall, 24x7x365, from our Secure Network Operations Center. Our technicians hold advanced vendor and security certifications that allow your institution to balance the security and operational functions of firewall management and maintaining your network.
Web Content Filtering: Blocking malicious web traffic in real-time
DataComm’s web content filtering solution was designed to eliminate the costly expenses and increasing cost of managing an in-house security appliance. Our service monitors and blocks malicious web traffic in real-time, making intelligent decisions that prevent employees from committing violations that could result in civil or criminal liability. Additionally, this service may improve the productivity of your staff by making sure that social media sites are only available to employees at certain times throughout the day.
Service Benefits
- Acceptable use controls let you define policies by user, group, IP, or domain; and also allows you to set time-based policies for Internet browsing during office hours, off-hours, or not at all – ensuring compliance to corporate web usage policies.
- Web application controls allow you to selectively permit or forbid use of web-based applications by individuals or groups, protecting your organization from non-productive applications and the malware they carry. This includes online chat rooms, popmail , gaming sites, wikis, blogs, and more.
- Advanced malware prevention scans web traffic for malicious content to prevent the infection and proliferation of web-based threats.
- Zero hour threat response closes the window of vulnerability between when an attack launches and when scanning filter updates are developed and distributed, extending the protection from new threats delivered via web channels.
- Attachment controls block harmful file types from entering your network via web-based traffic and applications.
- URL filtering analyzes and blocks access to websites based on pre-defined policies, using content control to block sites for reduced risks and legal liabilities.
- Dynamic inspection provides content filtering of uncategorized sites to bridge the security gap from where URL filtering capabilities end, providing an extensive web risk management boundary.
Log Monitoring: Monitoring mission critical servers
A common misconception is that security threats only come from external sources. A significant proportion of malicious activity actually originate from within an organization. Standard and necessary methods of protecting the network do very little to ensure the integrity of critical servers and workstations from an internal attack.
SecurLog, part of DataComm’s complete SecurSuite of services, was designed to combat this growing issue by monitoring event logs distributed by Windows and UNIX hosts. SecurLog utilizes trained security staff to monitor mission critical servers’ Event Viewer logs in real-time for policy and security violations, manage complex rulesets often overlooked when choosing standalone products and maintain logs required by regulators for critical devices. This service keeps your staff informed of internal security breaches without expensive applications, time-consuming installations and extensive training.
Service Features
- Comprehensive Event Collection provides application, system, & security event data on critical devices.
- Real-time Alerting & Notification generates alerts that allow you to set the specific criteria on hosts for which you need to be notified.
- Compliance Logging & Reporting creates predefined reports to meet HIPAA, GLBA and Sarbanes-Oxley requirements.
Vulnerability Scanning: Discover weaknesses before they can be exploited
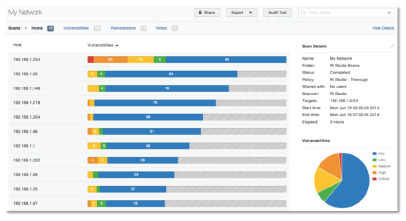
Vulnerability Assessments are an effective tool to combat the daily barrage of security threats and to help mitigate network changes that weaken your security posture. Vulnerability assessments augment annual penetration testing.
Oversight is key in all areas where a simple rule or configuration change can create devastating down-time or worse – a compromise of sensitive customer information. Our simple, yet necessary, solution can reduce or even remove concerns that a single user or group holds all the keys.
Service Features
- Weekly, Monthly or Quarterly Scheduled Scans
- Internal and/or External Scanning
- Thorough Assessment of Every Port and IP Address
- Comprehensive Reporting
- Seamless Integration with DataComm’s SecurSuite of Services