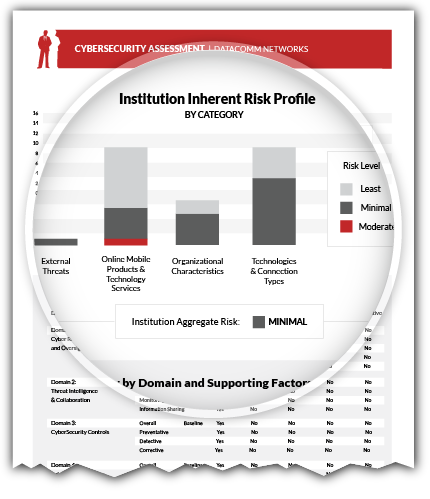
Audit Services: Verification, Remediation, & Reporting
We will perform an audit of one or all the below types to determine the effectiveness of your institution’s controls. The audit process will include examination of documents, sites and files, tests of control implementation and interviews with organizational personnel.
- IT Audits – Verification that your controls are working as designed is critical to your confidence in your information technology and security processes. We have experience with CoBIT and NIST frameworks.
- Cyber Security Risk Assessments – We can develop a risk assessment based upon the June 2015 FFIEC Cyber Security Risk Assessment or the June 2014 NIST Cyber Security Framework to identify and measure your cyber security risk profile.
- General Risk Assessments – We have performed numerous risk assessments to evaluate new and evolving services for our customers. We can help you pioneer new services safely.
- ACH Annual Audit – We provide an ACH Audit in accordance with NACHA requirements.
- Interest Rate Risk Independent Audit – We verify that it is effectively meeting business needs and FDIC regulatory guidance for interest rate risk management.
- Bank Secrecy Act Model Validations – We provide the most thorough BSA model validations that exceed standard compliance review. Our consultants verify model specifications, processes, authorizations, inputs, rules, calculations, and output for accuracy and effectiveness.
Compliancy with the Highest Regulatory Standards
We provide policies and standards that guide you in assessing and managing risk. We will tailor them to suit your institution’s complexity and needs.
- Vendor Management – We implement vendor management for you that is compliant with the toughest regulatory standards while keeping the process cost-effective.
- Business Continuity Management – We can implement and maintain an FFIEC compliant Business Continuity Plan that will allow you to maintain the availability of critical processes during foreseeable disasters.
- Incident Response – We can create a program for detection and analysis, containment eradication and recovery and post incident reporting that meets NIST standards and your needs (need technical support, notification support and a CFE or fraud expert).
- Policy Development – We provide policies that are tailored to meet your unique requirements.
- User Access – We can develop and maintain a successful user access process for you that provides user and vendor access without sacrificing the confidentiality of your data.
Penetration Testing: Let us test your network security before someone else does
As both the frequency and ingenuity of electronic attacks increase, so to does the need to regularly test the effectiveness of your information security controls. Theft of confidential data, such as client financial information and corporate secrets are no longer the sole objective of hackers as web site defacement now provides malicious individuals with a mechanism to degrade the public image of your institution. Penetration Testing remains a powerful tool to identify the vulnerabilities that may exist within your security architecture and gives you the opportunity to fix them before they are exploited.
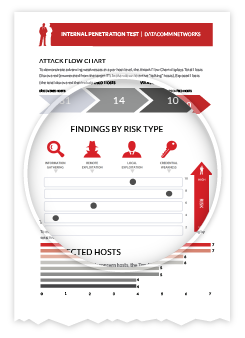
Detailed Reports with Recommended Solutions
- Comprehensive Reports – Our comprehensive and detailed reporting thoroughly document any exposures found during the course of penetration testing.
- Rapid Remediation – All exposure results are clearly documented with prioritized solutions enabling your institution to perform remediation rapidly.
Service Benefits
- Comprehensive Testing of Networks, Servers, Applications and Databases
- One of the Most Experienced and Respected Penetration Testing Teams
- Meets Federal Regulatory Requirements (GLB, SOX, HIPAA)
Types of Testing
- External Testing – Our security engineers utilize advanced techniques combined with a highly sophisticated testing platform, SecurScanner, to provide a holistic view of your current web facing security posture. By checking the available services, our staff is able to gain an accurate picture of what a potential malicious hacker would be presented with. The report is presented in an encrypted electronic format that can be archived for audit purposes.
- Internal Testing – To minimize the expense of an on-site assessment, a SecurScanner is shipped to your main office. A security engineer establishes an encrypted connection to the device and performs a thorough test of your internal network security controls. The report is delivered in the same encrypted format as the external test.
Vulnerability Scanning: Discover weaknesses before they can be exploited
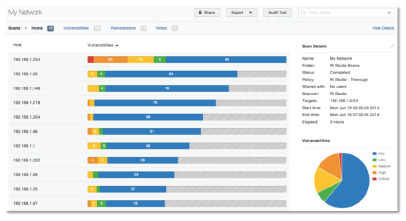
Vulnerability Assessments are an effective tool to combat the daily barrage of security threats and to help mitigate network changes that weaken your security posture. Vulnerability assessments augment annual penetration testing.
Oversight is key in all areas where a simple rule or configuration change can create devastating down-time or worse – a compromise of sensitive customer information. Our simple, yet necessary, solution can reduce or even remove concerns that a single user or group holds all the keys.
Service Features
- Weekly, Monthly or Quarterly Scheduled Scans
- Internal and/or External Scanning
- Thorough Assessment of Every Port and IP Address
- Comprehensive Reporting
- Seamless Integration with DataComm’s SecurSuite of Services